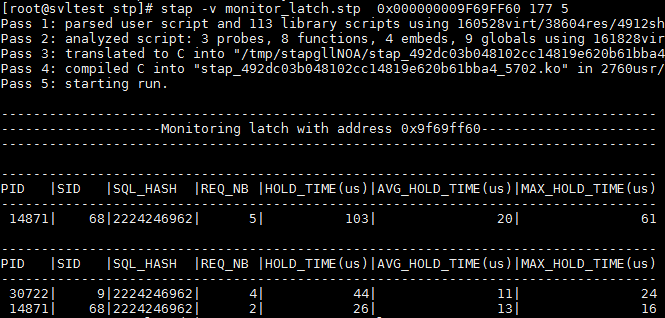
When troubleshooting a performance problem or investigating oracle internal using dynamic tracing tools like systemtap,it’s often useful to have the session address at hand. In fact, having the session address we can access many useful information such as : wait_event,p1 and p2 value,sql_id,and many other fields as stored in X$KSUSE (underlying table to V$SESSION). Luca Canali have already done a great work ,he identified that when the function “kskthewt” is called at the end of a wait event the register R13 (tested with Oracle 11.2.0.4 on RHEL6.5 and with Oracle 12.1.0.2 on OEL7 respectively) is pointing to the session addr with some offset and he manged also to determine the offset of the different column of X$KSUSE using X$KQFCO and X$KQFTA as in here.
The question is : Can we determine the session address without probing any function call ?
One way to answer this question is to determine how the value stored in the register R13 was set in the function “kskthewt”. Time to disassemble !
NOTE : This post contain no disassembly code of the oracle executable just the finding !
For basic info on reverse engineering please take look at my previous post.
Continue reading →